I recently got a question on how to use regex within vRealize Operations to make a symptom if DNS server settings on a host is incorrect. I did a quick google search and found out that info on regex and vROps wasn’t easily available. So here is a litte write up on the process.
Create the Symptom
First we need to create a symptom
Go to Configure, Alerts, Symptom Definitions and choose ADD
In the Add Symptom Definition view change Base Object Type to Host System and Symptom Type to Properties. In Select Specific Object expand Configuration, Network and double click on DNS Server.
Give the Symptom a resonable Name and on the If Property choose Does not match regular expression. In the Property value field you should now see the value we need to match.
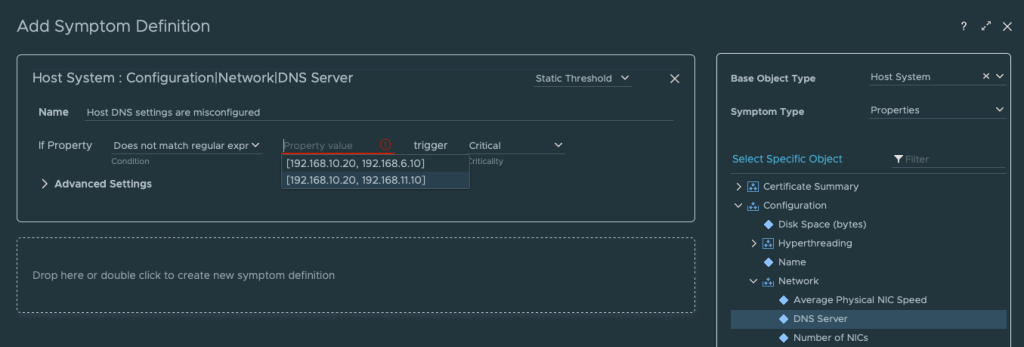
In my case the correct config is [192.168.10.20, 192.168.6.10] so I created a regex that will match on this value. There is probably other ways to create the regex but this worked for me. Regex example: \D192.168.10.20, 192.168.6.10\D
When that is done remember to set wanted Criticality and then save.
Create Alert Definitions
When that is done you can create your alert definitions and use the new symptom. (no step, by step guidance here)
More advanced reqex
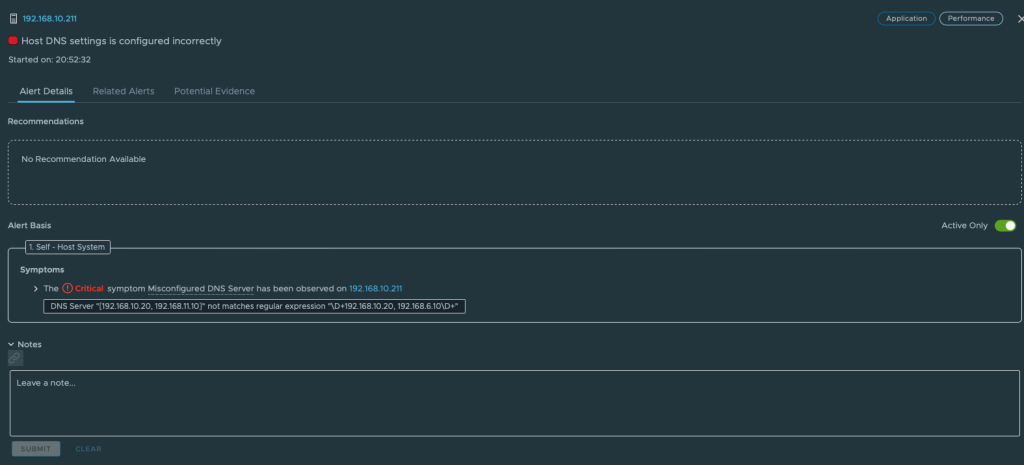
In my simple lab setup this regex was doing its job, but for a live production environment it might not be the case, what if some servers have the DNS configured in the opposite way? Then my regex won’t match.
That brings me to the customer use case brought to me by Bernt Christian Torbjørnsen, a vRealize Operations admin and virtualization evangelist. When combining my testing, some brainstorming and a screen sharing session with some trail and error we managed to tweak his regex to work within vROps and this is the code we ended up with.
RegEx: \D\b192.168.10.20\b.\b192.168.10.10\b\D|\D\b192.168.10.10\b.\b192.168.10.20\b\D
This regex will result in match if DNS servers is configure in any of thees to ways.
[192.168.10.20, 192.168.6.10] or [192.168.10.10, 192.168.6.20]
Hot Tip
If you want to test your expression quicker than waiting for vROps collection cycles, you can create a custom group instead and use your regex there to get instant preview.
In vRealize Operations it seems like we need to match the whole string including [ ] to get a match [192.168.10.20, 192.168.6.10]
Reference
https://regex101.com
Log Insight, Examples of Regular Expressions