You can do this from both vIDM (Workspace One Access) appliance or from the vRealize Suite Lifecycle Manager (vRSLCM) appliance. Changes done in one will sync to the other. In this walkthrough I will configure AD integration using vRSLCM.
Walkthrough
First you need to login as admin@local and go to Identity and Tenant Management then to Directories and Add Directory. Choose Active directory over LDAP
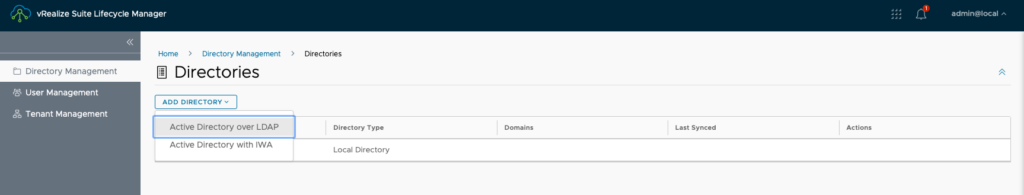
Insert your details as shown in picture below. when you have added all the details click the Test Connection button. If all is green you are good if not you need to start troubleshooting. Start with verifying that all the details indeed are correct.
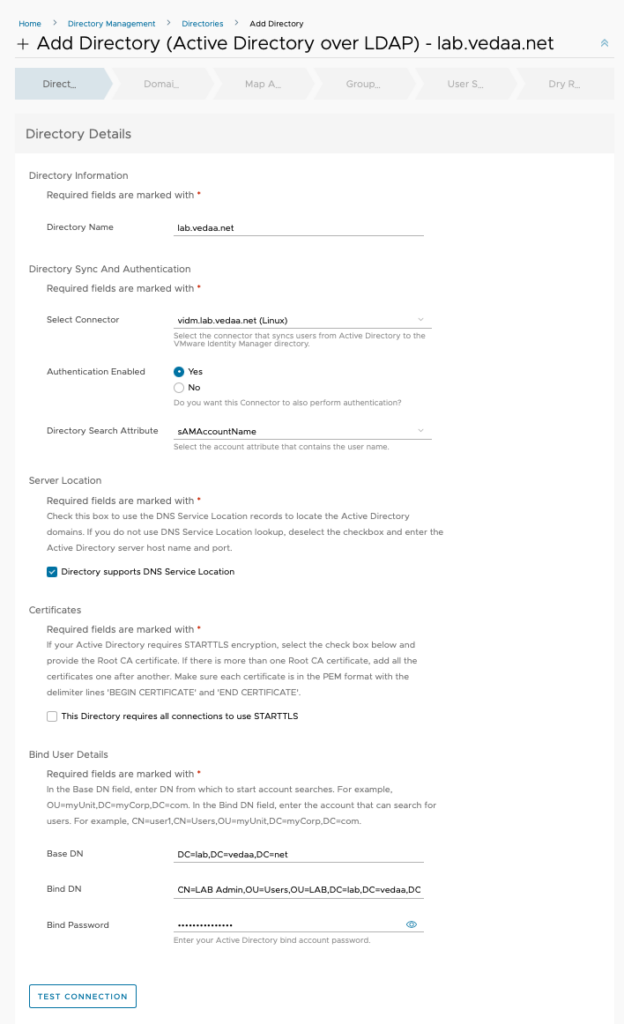
On the next screen verify that it has found the correct domain and click Save And Next
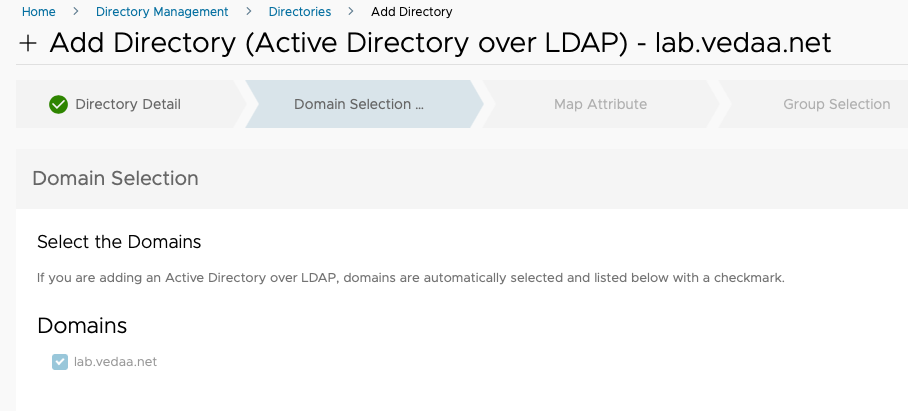
On the Attribute page you can choose to go with det defaults shown in this picture or you can make changes if needed. Click Save and Next.
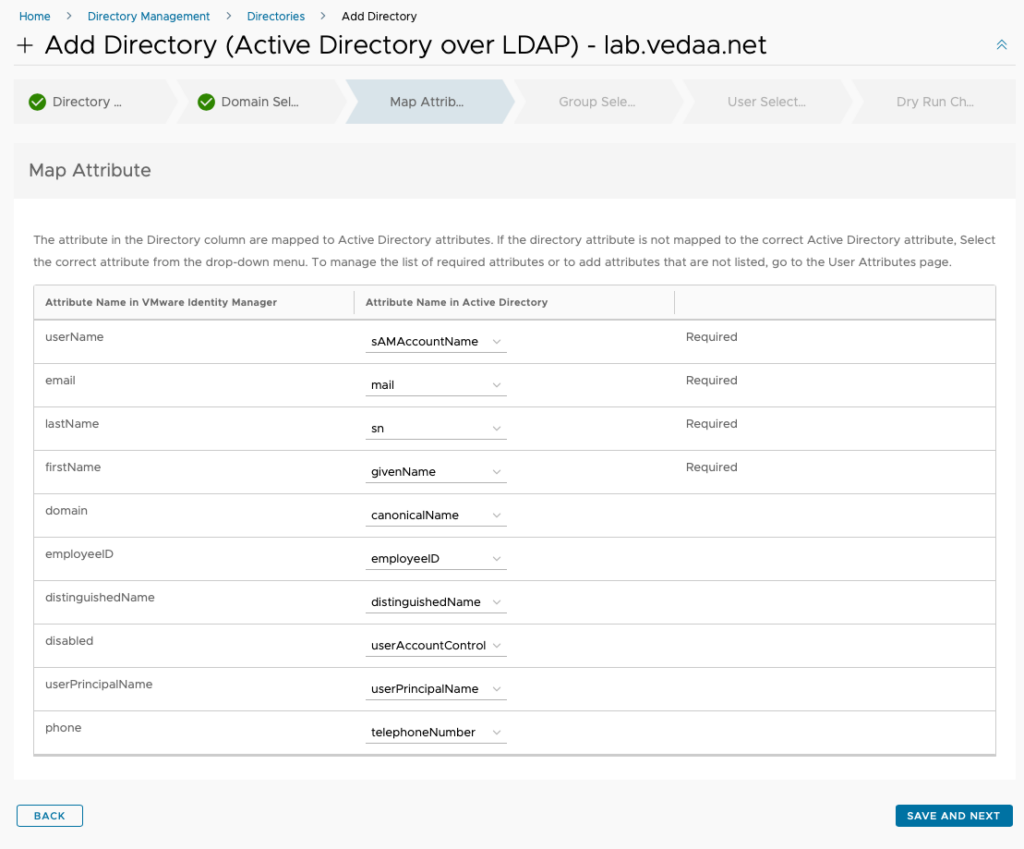
In the Group Selection section you must add a DNs for the groups you want to synchronize into vIDM. If you for some reason only want to add users you can do that in the next section. When you are satisfied with your selection click Save and Next.
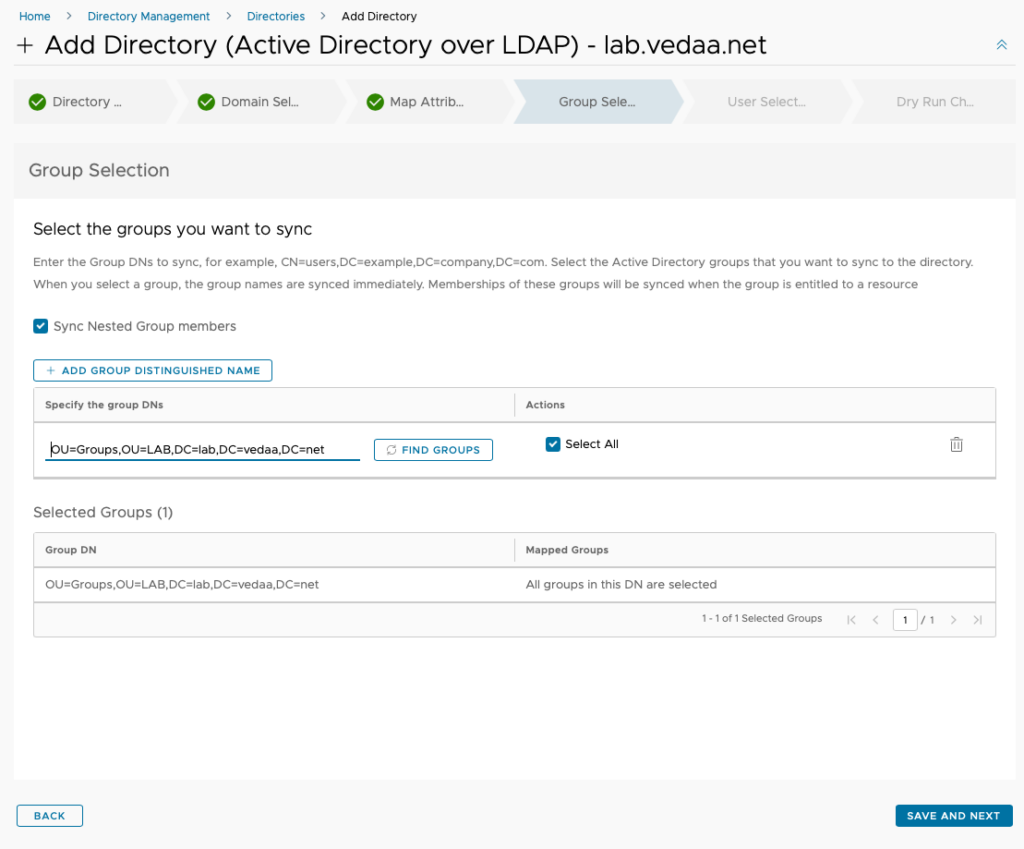
Select any users you want to sync that is not in any of your synced groups and click Save and Next
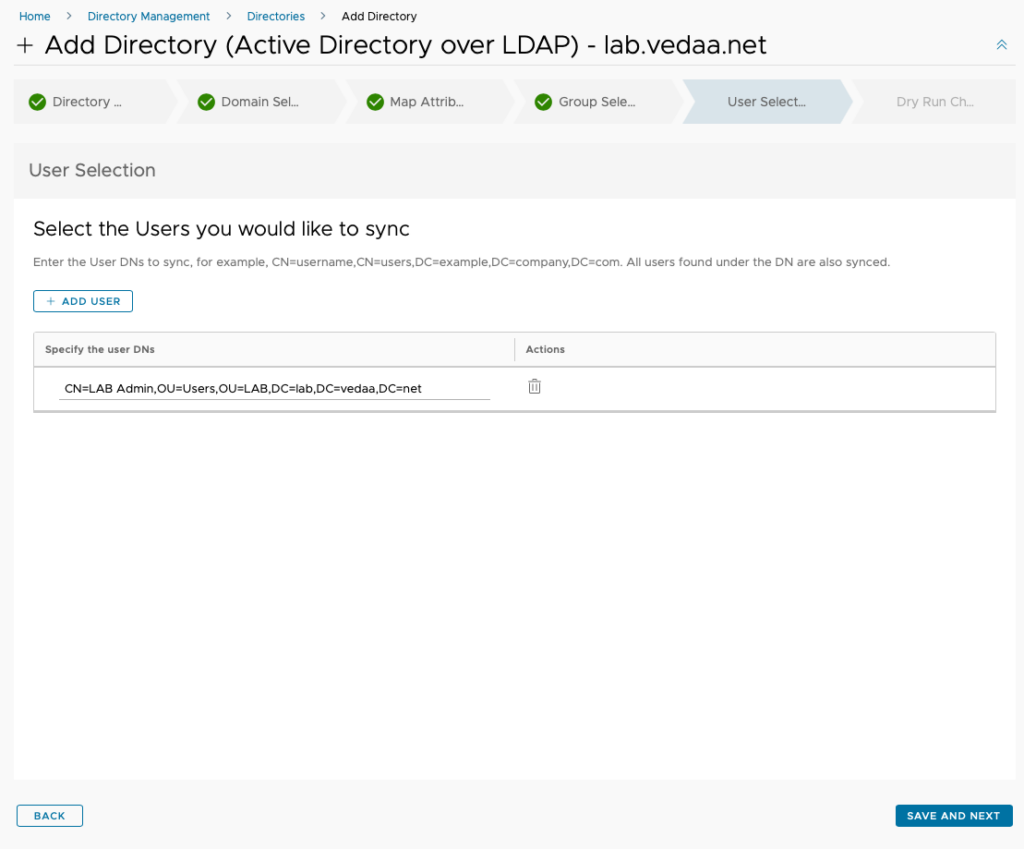
In this next section a dry run will be performed and you will get a summary of the users and groups that will be synced and a warning if any of the users don’t contain the required attributes and therefor cannot be synchronized. If you are not satisfied you can always click Back button and do changes. When you are happy click Sync and Complete.
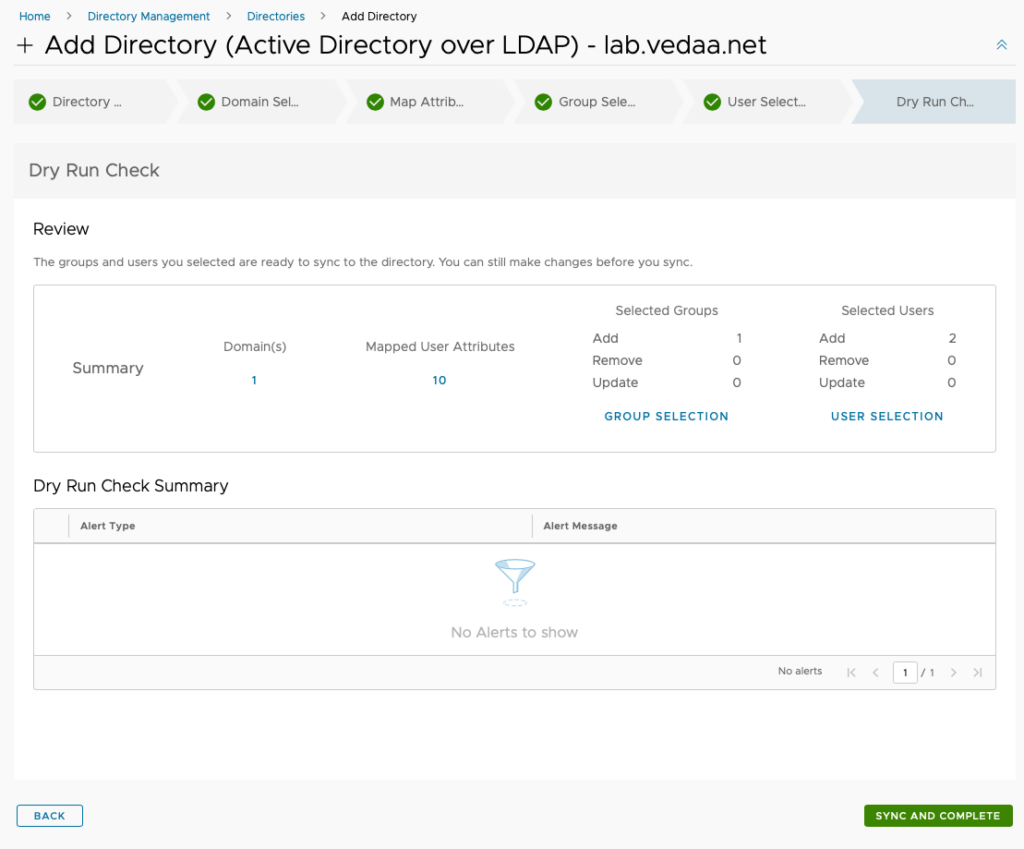
Summary
You can now use AD users and groups within Identity Manager.
It can be smart to go through the directory settings inside the vIDM appliance after setup to change Sync Frequency and other settings. By default the sync is once pr week.
True SSO
If you want to go further and enable true SSO for your users take a look at How to enable True SSO for vRealize Suite logins.